A couple of weeks ago, Netgear announced that there is a major security vulnerability in several router models that allows anyone within range of your wireless network to log in as administrator without credentials. So many things can go wrong if this happens to you. Even the US-CERT recommends that you don't use the router until you've updated it.
Check your home wireless router. Popular brands include Linksys, Asus, D-Link and Netgear, among others. If your manufacturer is Netgear, check which version you have and update your router with newer firmware asap.
The page listing the models and the steps to update the firmware is here: http://kb.netgear.com/000036386/CVE-2016-582384.
Even if you don't have a Netgear router, it is always a good idea to log in to your router occasionally to see if it needs a firmware update. Or set a Google alert that queries the manufacturer's name and model. Add the word "firmware" to your query and configure it to deliver a notification to you whenever there is new information available on the Internet.
For more information, see the Forbes article here: http://www.forbes.com/sites/leemathews/2016/12/12/these-netgear-routers-are-scarily-easy-to-hijack/#1f89ad0d9537.
Tips for being secure in today's digital world, and keeping your kids safe online as well.
Wednesday, December 28, 2016
Saturday, December 17, 2016
Advice if you use Yahoo: Don't.
By now the world knows about the one billion Yahoo accounts breached over the past three years. The best advice I've seen from the experts this week is "get rid of your Yahoo account." Likewise, if you have an account with Yahoo partner AT&T, consider cancelling that as well.
Tips for moving away from Yahoo:
- Back up your Yahoo data like old emails, contacts, calendar entries and photos. This includes Flickr photos. See instructions at: https://help.yahoo.com/kb/download-save-info-lose-good-sln15129.html.
- Delete your Yahoo folders.
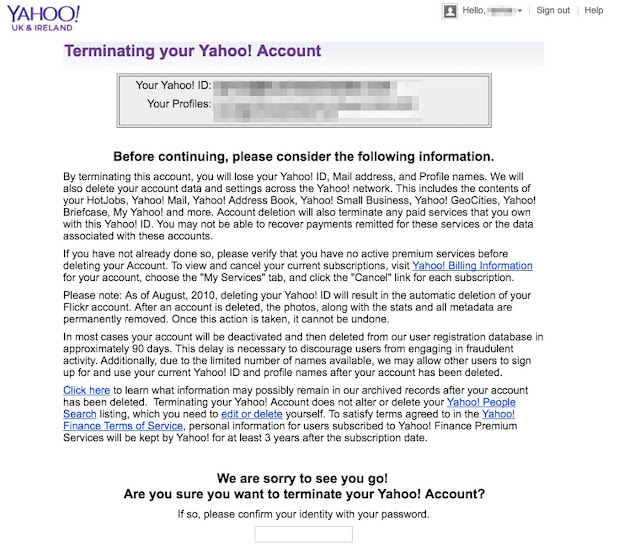
- Navigate to the Delete Your Account page at https://login.yahoo.com/?.done=https%3a%2f%2fedit.yahoo.com%2fconfig%2fdelete_user%3f.scrumb%3d0, and terminate your Yahoo account (see screen shot below). This can take up to 90 days to process.
After successfully terminating your Yahoo account:
- If you have ever used your Yahoo password for other sites–which is always a bad idea–change the password and security questions for those accounts. For sites holding really sensitive data (banking, insurance, taxes, medical, etc.), consider modifying your user name as well by appending or prepending it with a few characters, numbers or symbols (where allowed).
- If you have mobile phone number associated with your Yahoo account, and you still subscribe to that number, then you may be more prone to SMS phishing (a.k.a. smishing). Be on the alert for smishes and don't click links in text messages.
- Open a Gmail account.
Sunday, December 11, 2016
Don't get hacked this holiday season!
The holiday season is here. This is the time of year when scam artists are operating at full-tilt. Half of shoppers are buying gifts online this year. I've blogged about this in the past. This post is simply a reminder to be on your toes and to not share information about yourself with anyone who calls or emails you.
For tips in preventing identity theft and online scams, see the StaySafeOnline.org article Hackers Love the Holidays Too: How to Protect Yourself from Information and Identity Theft, summarized here.
Remember: Stop. Think. Do not click.
For tips in preventing identity theft and online scams, see the StaySafeOnline.org article Hackers Love the Holidays Too: How to Protect Yourself from Information and Identity Theft, summarized here.
- Avoid making purchases when using public Wi-fi.
- Never clicks links in unexpected, unusual or out-of-character emails - navigate to the web site directly from your browser. Just because an email looks like it is from someone you know doesn't mean it is legitimate.
- Never download or open attachments sent to you in email.
- Use anti-virus software and activate the firewall on your operating system.
- Delete unused accounts on web e-commerce and other sites where possible.
Remember: Stop. Think. Do not click.
Wednesday, November 23, 2016
Watch out: ɢoogle.com isn’t the same as Google.com
It isn't unusual for bad guys to buy fake domain names that resemble real ones. Often they use simple character substitution.
For example, in h0medep0t.com, you'll notice there is a zero (0) where there should be a letter O. Although this example looks pretty obvious, often we don't take time to scrutinize what's in the address bar of the web browser.
Or, we jump to the link without looking closer, such as in an email or a text message where the real URL doesn't match up with the link displayed. In most email programs, like Microsoft Outlook, you can hover over the displayed link with your mouse cursor to see the actual web location that the link redirects you to—the URL—but this feature isn't available in all operating systems or in all email clients. You won't necessarily have this ability on your smart phone or web email client, for example.
This is why I don't click links sent to me—even from people I know—without scrutinizing them first. Here is a PCWorld article with more information about validating links: http://www.pcworld.com/article/248963/how_to_tell_if_a_link_is_safe_without_clicking_on_it.html.
Here is more about the Google scam. Scammers use a domain name that looks like Google.com but isn't: ɢoogle.com. Look at the "G." It isn't a standard letter that you'd type on a keyboard. It is actually a symbol, which uses a different character set. International (or extended) characters like this one are rendered on your computer screen by typing a specific combination of keys and numbers on a standard keyboard.
For more info, do a web search on the phrase "character set."
Here is the full article about the bad ɢoogle.com:
http://www.analyticsedge.com/2016/11/heres-a-secret-%C9%A2oogle-com-is-not-google-com/.
For example, in h0medep0t.com, you'll notice there is a zero (0) where there should be a letter O. Although this example looks pretty obvious, often we don't take time to scrutinize what's in the address bar of the web browser.
Or, we jump to the link without looking closer, such as in an email or a text message where the real URL doesn't match up with the link displayed. In most email programs, like Microsoft Outlook, you can hover over the displayed link with your mouse cursor to see the actual web location that the link redirects you to—the URL—but this feature isn't available in all operating systems or in all email clients. You won't necessarily have this ability on your smart phone or web email client, for example.
This is why I don't click links sent to me—even from people I know—without scrutinizing them first. Here is a PCWorld article with more information about validating links: http://www.pcworld.com/article/248963/how_to_tell_if_a_link_is_safe_without_clicking_on_it.html.
Here is more about the Google scam. Scammers use a domain name that looks like Google.com but isn't: ɢoogle.com. Look at the "G." It isn't a standard letter that you'd type on a keyboard. It is actually a symbol, which uses a different character set. International (or extended) characters like this one are rendered on your computer screen by typing a specific combination of keys and numbers on a standard keyboard.
For more info, do a web search on the phrase "character set."
Here is the full article about the bad ɢoogle.com:
http://www.analyticsedge.com/2016/11/heres-a-secret-%C9%A2oogle-com-is-not-google-com/.
Saturday, November 19, 2016
Beware fake phone calls from "customer service"
It cannot be said enough: hang up on callers whom you do not know, especially if they are trying to elicit any information from you. Better yet, if you don't recognize the phone number of the caller, don't pick up. Scam artists are less likely to try again if you're not answering.
Protect yourself and your employer by taking advantage of Caller ID service on your phone. Personally, if a call comes in to my cell phone from an unknown number, I let it go to voice mail.
It seems there is a new phone scam every day. Reported by Trustwave this week is a ruse that targets hotel and restaurant chains. This scam is perpetrated by a known cyber criminal gang that employs very convincing social engineering techniques like name-dropping and familiarity with other "insider" knowledge about your org chart.
When the caller reaches the hotel or restaurant's customer service line by phone, he/she claims to be a client who cannot log in to the reservations system. The caller may claim to know your boss or C-level executive.
Remember that this type of information about your company is available on the web to anyone. It takes little effort to mine LinkedIn profiles and gather intelligence about your organization's personnel structure.
An email is sent to the customer service rep with a malicious Microsoft Word document attached. When clicked, malware is executed behind the scenes that provides access to the company's credit card database and other sensitive information.
Click here for the story: This malware attack starts with a fake customer service call. When in doubt, just hang up!
Protect yourself and your employer by taking advantage of Caller ID service on your phone. Personally, if a call comes in to my cell phone from an unknown number, I let it go to voice mail.
It seems there is a new phone scam every day. Reported by Trustwave this week is a ruse that targets hotel and restaurant chains. This scam is perpetrated by a known cyber criminal gang that employs very convincing social engineering techniques like name-dropping and familiarity with other "insider" knowledge about your org chart.
When the caller reaches the hotel or restaurant's customer service line by phone, he/she claims to be a client who cannot log in to the reservations system. The caller may claim to know your boss or C-level executive.
Remember that this type of information about your company is available on the web to anyone. It takes little effort to mine LinkedIn profiles and gather intelligence about your organization's personnel structure.
An email is sent to the customer service rep with a malicious Microsoft Word document attached. When clicked, malware is executed behind the scenes that provides access to the company's credit card database and other sensitive information.
Click here for the story: This malware attack starts with a fake customer service call. When in doubt, just hang up!
Sunday, November 6, 2016
Election scams - Don't fall for them
It is officially election week in the United States. This opens up lots of opportunities for social engineers and crooks to take advantage of voters. Emotions are high right now, making it tough for us to be at our best, but this is exactly the time to be vigilant.
Be on the lookout for online scams and, as a rule, just don't click. Phone scams abound too—just hang up.
For example, if you receive a message inviting you to vote by texting, forget it. Delete the message. You can't sit in your living room and click a link to vote—at least, not this year. You also cannot vote by phone.
Stay on the lookout for last-minute "urgent" messages saying that your voter registration has expired or your polling station has moved. Ignore requests for last-minute donations to win the election in your party's favor.
Another good way to be duped is through fake email messages purporting to deliver the latest election results. Do not click links or attachments! If you want to know the latest, navigate to your favorite news site in your web browser, or turn on your TV. Don't ever expect emailed or texted links about news articles to be legitimate.
For more information, see the November 3 Huffington Post article: Watch out for these last-minute election scams.
Stop. Think. Do not click!
Be on the lookout for online scams and, as a rule, just don't click. Phone scams abound too—just hang up.
For example, if you receive a message inviting you to vote by texting, forget it. Delete the message. You can't sit in your living room and click a link to vote—at least, not this year. You also cannot vote by phone.
Stay on the lookout for last-minute "urgent" messages saying that your voter registration has expired or your polling station has moved. Ignore requests for last-minute donations to win the election in your party's favor.
Another good way to be duped is through fake email messages purporting to deliver the latest election results. Do not click links or attachments! If you want to know the latest, navigate to your favorite news site in your web browser, or turn on your TV. Don't ever expect emailed or texted links about news articles to be legitimate.
For more information, see the November 3 Huffington Post article: Watch out for these last-minute election scams.
Stop. Think. Do not click!
Wednesday, October 12, 2016
IRS form CP2000 scam and Hurricane Matthew scams
If
you receive an email with an IRS CP 2000 form and a claim that the
income reported on your tax return does not match the income reported by your
employer, it is a scam. The message may also indicate that your issue is related to the
Affordable Care Act.
Of course, the IRS will never initiate contact with you to
collect overdue taxes by email, text message or phone call. If you receive such a text or email, don’t respond. If they call, hang up. If
you receive a CP 2000 form in the U.S. mail and you question whether it’s legit, call
the IRS at 1-800-366-4484.
Also,
watch out for scam and malware messages related to the hurricane. One bogus
email that is being distributed now claims that you can click a link to find out about power
outages in your area. Other Hurricane Matthew related malware messages
may be distributed in the coming days and weeks, including requests for
donations. Emails or social media posts may offer links to read news reports
about the hurricane. Even if these messages appear to come from CNN or another
news outlet, don’t trust them. Stay alert!
Sunday, September 25, 2016
Yahoo account holders, you need to do more than just reset your password
By now everyone has heard of the 500 million Yahoo accounts that were hacked and leaked online. CNN story here.
See these Sophos tips for creating passwords. If you're really ambitious, you can take it one step further and use unique user names for the sites that hold your most sensitive data.
If you get any email related to the breach, just delete it. Don't reply to it, don't forward it, and don't click any links or open any attachments in the message.
What to do
Of course, if you have a Yahoo login that you use for any purpose (e.g., Yahoo email, Yahoo groups, Yahoo shopping, etc.), you need to navigate to Yahoo.com in your web browser and reset your password to a strong password. While you're at it, reset your security questions and answers and enable two-factor authentication using Yahoo Account Key.See these Sophos tips for creating passwords. If you're really ambitious, you can take it one step further and use unique user names for the sites that hold your most sensitive data.
What not to do
Do not use that same user name and password combination on any other sites.What else?
Be on the alert for phishing emails that exploit this "world's biggest hack" story. Scammers will try take advantage of situations like this by emailing users fake messages that are designed to steal your login credentials or banking information.If you get any email related to the breach, just delete it. Don't reply to it, don't forward it, and don't click any links or open any attachments in the message.
Thursday, September 15, 2016
New type of tech support fraud: Email tells you to call toll-free number
In the last few years, web service providers like Google, Yahoo and Facebook have started sending emails to users to warn them when there is a possible security risk to their account, like an impersonator logging in from an unknown computer.
In the past, bad guys would copy these emails into phishing messages that trick you into logging in to a fake website where they steal your user name and password. Now, these fake security emails give you a toll-free (800) number that they claim you need to call immediately.
If you call the number, two things could happen:
If you ever need to call a vendor, use your web browser to navigate to the trusted vendor URL and call the number listed on the legitimate web page. Never use a phone number provided in an email.
Here is a link to a sample (and humorous) fake phone call, click here: http://cdn2.hubspot.net/hubfs/241394/phone_phish.mp3.
In the past, bad guys would copy these emails into phishing messages that trick you into logging in to a fake website where they steal your user name and password. Now, these fake security emails give you a toll-free (800) number that they claim you need to call immediately.
If you call the number, two things could happen:
- You get to talk with a real cyber criminal, typically with a foreign accent, who tries to scam you. He or she claims there is a problem with your computer then "fixes" it and asks for your credit card info.
- You get sent to to voice mail or are put on hold until you hang up, but your phone number was recorded and stored in a queue; the bad guys then call you back and try the same scam.
If you ever need to call a vendor, use your web browser to navigate to the trusted vendor URL and call the number listed on the legitimate web page. Never use a phone number provided in an email.
Here is a link to a sample (and humorous) fake phone call, click here: http://cdn2.hubspot.net/hubfs/241394/phone_phish.mp3.
Friday, September 2, 2016
Beware email with .DOCM or .DOCX (Microsoft Word) documents attached
According to FireEye, the strain of ransomware called Locky resurfaced a few weeks ago. If you click the Word document attached to the Locky email, it runs a program that encrypts all your files, renaming each with the .locky extension. You have to pay up to get the decryption key that restores your files.
Below are screen shots of sample Locky ransomware emails. For a better view, click the image here, or go to the FireEye article at https://www.fireeye.com/blog/threat-research/2016/08/locky_ransomwaredis.html.
A new variant reported three days ago in the SANS ISC InfoSec Forums uses the subject line "Transaction details." While the email generally looks the same as those pictured here, the attachment is a ZIP file containing a compressed Windows Script File (.wsf).
Any time you receive an email from anyone that contains an attachment or links, stop and take your hands off your mouse and keyboard. You do not want to click anything that is even remotely suspicious or unexpected. When in doubt, delete.
For more information, see "Locky" ransomeware - what you need to know.
Below are screen shots of sample Locky ransomware emails. For a better view, click the image here, or go to the FireEye article at https://www.fireeye.com/blog/threat-research/2016/08/locky_ransomwaredis.html.
Any time you receive an email from anyone that contains an attachment or links, stop and take your hands off your mouse and keyboard. You do not want to click anything that is even remotely suspicious or unexpected. When in doubt, delete.
For more information, see "Locky" ransomeware - what you need to know.
Tuesday, August 23, 2016
Beware of "FTC Refund" phishing fraud
There is a new email scam out that is based on a previous scam perpetrated by J.K. Publications, Inc., that was resolved by the Federal Trade Commission (FTC) several years back.
Because the FTC publishes fraudulent cases like this one on its web site, bad guys can use this information to create a phishing attack that appears legitimate. The real FTC cases are posted here: https://www.ftc.gov/enforcement/cases-proceedings/refunds.
The phishing email being disseminated this week appears to be from the FTC; it recounts old facts from the J.K. Publications case and promises you a refund check. However, the FTC will not send you an email telling you that you need to take action (like click a link or attachment in the email) to receive a refund.
Rule of thumb: Any time you receive an email from an official-sounding organization promising you a refund in a particular dollar amount, be extremely wary of it. Do not click links and do not open attachments to emails like this. Delete the email.
Because the FTC publishes fraudulent cases like this one on its web site, bad guys can use this information to create a phishing attack that appears legitimate. The real FTC cases are posted here: https://www.ftc.gov/enforcement/cases-proceedings/refunds.
The phishing email being disseminated this week appears to be from the FTC; it recounts old facts from the J.K. Publications case and promises you a refund check. However, the FTC will not send you an email telling you that you need to take action (like click a link or attachment in the email) to receive a refund.
Rule of thumb: Any time you receive an email from an official-sounding organization promising you a refund in a particular dollar amount, be extremely wary of it. Do not click links and do not open attachments to emails like this. Delete the email.
Monday, August 15, 2016
Two "MySSA" Social Security Administration phishing scams to watch for
Description (official SSA.gov alert is here)
- In the first scam, you receive an official-looking email from the Social Security Administration (SSA), inviting you to create an account so you can receive benefits. The link lands you on a fraudulent web page where scammers hope you will input your confidential information.
- In the second scam, the bad guys actually create an account for you and then redirect payments to a bank account that they control.
Prevention tips:
- As always, stop, think and do not click! Navigate to ssa.gov directly from your web browser.
- Create your own MySSA account with a strong username and password at https://secure.ssa.gov/RIL/SiView.do. This is similar to filing your tax return early before the bad guys file a bogus return and steal your refund.
- When creating your MySSA account, under Add extra security, enable two-factor authentication via text message.
- After you create your MySSA account, go to settings and choose the option that any changes to your bank account be done physically at a SSA branch office instead of using your online account.
- Alternatively, block all electronic access to your Social Security record. See https://secure.ssa.gov/acu/IPS_INTR/blockaccess. To unblock your record in the future requires contacting the SSA.
Saturday, August 6, 2016
See how quickly a social engineer can nab your account credentials
This time every year, a couple of ginormous cyber security conferences happen in Las Vegas. Thousands of hackers and information security geeks gather to attend the infamous DEF CON and Black Hat events. Some of the hacks that are revealed at these events each year will astound the average Internet user—including demonstrations of hacking a baby monitor, remotely shutting down an insulin pump, building a hacker drone, using a cell phone to hack a car, etc.
And let's face it, we are all Internet users now because most of our electronic devices are connected to the Internet. This is called the Internet of Things, or IoT.
The most common cyber attack vector employs social engineering techniques to get you to unwittingly execute malware that exploits some vulnerability in your system, allowing someone to remotely control the system or perhaps encrypt all your files and hold them for ransom, and other nefarious deeds.
Social engineers use deception to persuade you into giving up information that you should not be sharing. This is very easily achieved. Embedded in this Tech Insider article is a 10-minute real-world video to prove it: A hacker shows how you can take over someone's online account in minutes using nothing but a phone.
Watch this hacker steal a reporter's cellular account credentials and email address in only moments with one phone call to his cellular carrier.
And let's face it, we are all Internet users now because most of our electronic devices are connected to the Internet. This is called the Internet of Things, or IoT.
The most common cyber attack vector employs social engineering techniques to get you to unwittingly execute malware that exploits some vulnerability in your system, allowing someone to remotely control the system or perhaps encrypt all your files and hold them for ransom, and other nefarious deeds.
Social engineers use deception to persuade you into giving up information that you should not be sharing. This is very easily achieved. Embedded in this Tech Insider article is a 10-minute real-world video to prove it: A hacker shows how you can take over someone's online account in minutes using nothing but a phone.
Watch this hacker steal a reporter's cellular account credentials and email address in only moments with one phone call to his cellular carrier.
Monday, July 25, 2016
Beware cyber scams around the Olympics
According to the Weekly Digest Bulletin issued by the Department of Homeland Security (DHS), we should all be on the lookout for cyber scams about Rio 2016. These can come to you via fake web sites, phishing emails or SMS text messages—perhaps even by phone.
Only input your credit card or other personal information on web sites that you know and trust. Watch out for fake domain names containing "rio" or "rio2016" in the address bar of your web browser. Think before you click.
Inform yourself. For more details about the following types of scams, see this RSA blog entry: https://blogs.rsa.com/cyber-scams-to-beware-of-at-the-2016-summer-olympics/:
What do do?
Stay on your toes and be wary of any message that you receive or encounter about Olympics tickets or merchandise while connected to the Internet. Remember, these can present themselves as ads on just about any web page you visit.Only input your credit card or other personal information on web sites that you know and trust. Watch out for fake domain names containing "rio" or "rio2016" in the address bar of your web browser. Think before you click.
Inform yourself. For more details about the following types of scams, see this RSA blog entry: https://blogs.rsa.com/cyber-scams-to-beware-of-at-the-2016-summer-olympics/:
- Fake tickets to Rio 2016 Olympics
- You've won tickets to Rio 2016
- Counterfeit Olympics merchandise
- Mobile threats
Saturday, July 23, 2016
Using Apple devices? Update them today
If you have an iPhone, iPad, Mac, Apple TV or Apple Watch, it's a good idea to update the device right now. Today.
The flaw being discussed in the news this week allows a hacker in through a simple text message or email sent to your Apple device. Once in your system, the attacker can take over your device.
Depending on your configuration, if your device is set to display images automatically, which is the default setting, no user interaction with the malicious message is required for the hack to be successful. All the user has to do is open the tainted message, thereby rendering the exploit-tinged image contained in the message. This makes the attack difficult to detect.
On your iOS device, use the Settings app to update the operating system.
For more information, see iOS flaw lets hackers access iPhones using an iMessage. The video is quite helpful.
The flaw being discussed in the news this week allows a hacker in through a simple text message or email sent to your Apple device. Once in your system, the attacker can take over your device.
Depending on your configuration, if your device is set to display images automatically, which is the default setting, no user interaction with the malicious message is required for the hack to be successful. All the user has to do is open the tainted message, thereby rendering the exploit-tinged image contained in the message. This makes the attack difficult to detect.
On your iOS device, use the Settings app to update the operating system.
For more information, see iOS flaw lets hackers access iPhones using an iMessage. The video is quite helpful.
Saturday, July 16, 2016
Pokémon Go: Understanding the security and safety risks
You have probably
heard about the new Pokémon app, which has gone viral. Pokémon Go sends smart phone users out onto the
street to real-world locations (called PokéStops) in order to 'catch' little virtual creatures. The game gives the app access to your GPS location, camera, and more.
Adults, know that there are some risks if you have succumbed to the "gotta catch 'em all" fever, and talk to your children about it.
Adults, know that there are some risks if you have succumbed to the "gotta catch 'em all" fever, and talk to your children about it.
- First, download the app only from trustworthy app stores (i.e., Google Play, Apple App & iTunes, etc.); do not download the app from anywhere else. Why? Bad guys have created fraudulent look-alike versions of the app, infected them with malware, and are trying to trick you into downloading the fake apps from untrustworthy websites.
- Second, anyone using the app—especially kids—should be very careful not to be lured into a real-world trap that could lead to mugging or abduction. Other players can track you in the real world using this app, so be mindful of where you are going, at what time of day/night, and with whom. Stay alert.
- Third, there are possible privacy issues if you use your Google account to log into the app. Create a separate throw-away account that you use only to log into Pokémon; do not use not your private account or business account.
As always, think before you click! For more information, see The security risks of Pokémon Go, explained.
Thursday, July 7, 2016
Do you cover your laptop "webcam" lens?
Many people I know use a sliding webcam cover to prevent a hacker from viewing through the computer's camera. Facebook founder Mark Zuckerberg does this, too. Not to mention, he covers his computer's microphone. Covering the mic is new to me, but it makes sense because, just as a camera can be hacked into, so can a microphone.
A while back, while visiting my mom, I applied an adhesive webcam cover to her laptop. If you're a frequent webcam user (i.e., you use Skype or similar video-enabled apps), then you'll want to adhere a sliding webcam cover to surface of your laptop, like the one pictured below. Or, if you do not use your webcam, black electrical tape works fine.

A good friend of mine shared a recent New York Times article with me, where the reporter raises the question: Is this is paranoia or just good practice?
Ask yourself this: If you close your window blinds to ward off burglars, is that paranoia or good practice? Any physical security expert will tell you that it's the smart thing to do, as thieves are less likely to hit the house on the street that they cannot see inside.
If you're a high-value target, like Mark Zuckerberg attending a conference, then you definitely want to cover both the mic and the camera. Home users, you should keep your camera covered when not in use. Obscuring the mic certainly cannot hurt.
You be the judge—here is the article: Mark Zuckerberg Covers His Laptop Camera. You Should Consider It, Too.
NOTE: The mic is not the same thing as the microphone input jack port used to plug in an external microphone. If you aren't sure where your microphone input is on your laptop, consult the manufacturer's manual. If you can't find the manual, just Google the make and model number. It's there.
A while back, while visiting my mom, I applied an adhesive webcam cover to her laptop. If you're a frequent webcam user (i.e., you use Skype or similar video-enabled apps), then you'll want to adhere a sliding webcam cover to surface of your laptop, like the one pictured below. Or, if you do not use your webcam, black electrical tape works fine.

A good friend of mine shared a recent New York Times article with me, where the reporter raises the question: Is this is paranoia or just good practice?
Ask yourself this: If you close your window blinds to ward off burglars, is that paranoia or good practice? Any physical security expert will tell you that it's the smart thing to do, as thieves are less likely to hit the house on the street that they cannot see inside.
If you're a high-value target, like Mark Zuckerberg attending a conference, then you definitely want to cover both the mic and the camera. Home users, you should keep your camera covered when not in use. Obscuring the mic certainly cannot hurt.
You be the judge—here is the article: Mark Zuckerberg Covers His Laptop Camera. You Should Consider It, Too.
NOTE: The mic is not the same thing as the microphone input jack port used to plug in an external microphone. If you aren't sure where your microphone input is on your laptop, consult the manufacturer's manual. If you can't find the manual, just Google the make and model number. It's there.
Saturday, July 2, 2016
The Big Hack: Can this happen to us?
In June, New Yorker Magazine published a gripping tale depicting a coordinated cyber attack against New York City. Reeves Weideman's story is a fictional account based on real-life hacks and attacks that already exist today.
Carrying out this type of attack would require well-corroborated resources and a highly sophisticated plan. But every vector of attack laid out in this story is one that is feasible. It is the coordination and timing of the various cyber attacks that make this story so fantastic.
Can it happen? Sure. Will it happen in our lifetimes? I don't know. But 9/11 happened; that synchronized attack required just five years of planning.
I share this story with you today not to incite fear but to educate. We live in a world where every modern convenience is connected to the Internet, and we each need to understand the security implications of that ubiquity.
Our HOA property manager was on site (for once) the other day, telling me that he knows exactly how to prevent being hacked. "I tell everyone to just shut down their computers," he proudly opined. Sure, if you are unplugged from the Internet permanently, you'll never get hacked.
Good luck with that. This fellow couldn't run his business without Internet connectivity.
It's a naive suggestion because every electronic device you own now and in the future is already connected to the Internet, including the phone in your pocket. Better to educate yourself and be vigilant.
Here is that New Yorker story: The Big Hack: Envisioning the Hack That Could Take Down NYC: The day cars drove themselves into walls and the hospitals froze. A scenario that could happen based on what already has.
Carrying out this type of attack would require well-corroborated resources and a highly sophisticated plan. But every vector of attack laid out in this story is one that is feasible. It is the coordination and timing of the various cyber attacks that make this story so fantastic.
Can it happen? Sure. Will it happen in our lifetimes? I don't know. But 9/11 happened; that synchronized attack required just five years of planning.
I share this story with you today not to incite fear but to educate. We live in a world where every modern convenience is connected to the Internet, and we each need to understand the security implications of that ubiquity.
Our HOA property manager was on site (for once) the other day, telling me that he knows exactly how to prevent being hacked. "I tell everyone to just shut down their computers," he proudly opined. Sure, if you are unplugged from the Internet permanently, you'll never get hacked.
Good luck with that. This fellow couldn't run his business without Internet connectivity.
It's a naive suggestion because every electronic device you own now and in the future is already connected to the Internet, including the phone in your pocket. Better to educate yourself and be vigilant.
Here is that New Yorker story: The Big Hack: Envisioning the Hack That Could Take Down NYC: The day cars drove themselves into walls and the hospitals froze. A scenario that could happen based on what already has.
Friday, June 24, 2016
If Comcast calls, hang up!
Typically, Comcast doesn't call you unless they are trying to sell you something. Or maybe to survey you following a recent customer service experience. Today's story describes one situation where you definitely do not want to engage a purported Comcast rep who initiates a call with you.
My sister texted me this afternoon to say that someone claiming to be from Comcast called her and told her that her email has been reported as sending spam and pornography from Nigeria, Mexico and New Jersey. The caller had her run a command prompt (as Administrator, no less) and run the netstat command. Here is some sample output from that command:

Anyone who has used netstat knows that the output has a column heading called "Foreign Address." Based on my sister's story, it is clear that scammers are using that information to mislead unsuspecting computer users into thinking their computer is communicating with "foreign" computers. Hogwash.
My sister, who is not a "tekkie," was alert enough to put a halt to things right there, asking the guy to provide proof he is a Comcast employee. Wisely, she asked him to tell her what her account number is. He could not do that and hung up.
This is a very common "setup" that is staged to convince you something is wrong with your computer that you need to fix right away. From here, the hacker normally talks you into remotely accessing your computer, whereby he plants malware, such as a remote access Trojan, a keystroke logger, or ransomware on your computer. Or he gets a credit card number from you to charge you for fixing your problem.
I told my sister she did the right thing but that she needs to stay on her toes going forward because these guys will try again. She said she plans on changing all her passwords immediately, just to be safe. It's a good idea to change your passwords occasionally, so I couldn't agree with her more.
Remember, anyone who phones you to say your computer is infected with a virus or is showing up on their monitors as routing data to foreign countries, or anything similar to that, is a scammer. Hang up!
User: 1 - Hacker: 0.
I love a happy ending.
My sister texted me this afternoon to say that someone claiming to be from Comcast called her and told her that her email has been reported as sending spam and pornography from Nigeria, Mexico and New Jersey. The caller had her run a command prompt (as Administrator, no less) and run the netstat command. Here is some sample output from that command:
Anyone who has used netstat knows that the output has a column heading called "Foreign Address." Based on my sister's story, it is clear that scammers are using that information to mislead unsuspecting computer users into thinking their computer is communicating with "foreign" computers. Hogwash.
My sister, who is not a "tekkie," was alert enough to put a halt to things right there, asking the guy to provide proof he is a Comcast employee. Wisely, she asked him to tell her what her account number is. He could not do that and hung up.
This is a very common "setup" that is staged to convince you something is wrong with your computer that you need to fix right away. From here, the hacker normally talks you into remotely accessing your computer, whereby he plants malware, such as a remote access Trojan, a keystroke logger, or ransomware on your computer. Or he gets a credit card number from you to charge you for fixing your problem.
I told my sister she did the right thing but that she needs to stay on her toes going forward because these guys will try again. She said she plans on changing all her passwords immediately, just to be safe. It's a good idea to change your passwords occasionally, so I couldn't agree with her more.
Remember, anyone who phones you to say your computer is infected with a virus or is showing up on their monitors as routing data to foreign countries, or anything similar to that, is a scammer. Hang up!
User: 1 - Hacker: 0.
I love a happy ending.
Wednesday, June 15, 2016
Beware fake charitable organizations asking for your money to help victims
It saddens us all greatly to witness the tragedies that unfolded
in the Orlando area this week. As humans, we all want to do what we can to help.
Being a good distance away from the scene, often our assistance is provided
through funding various support and recovery efforts.
However, be aware that after any large-scale event like this
one, often the con artists are the first to set up shop. Don’t give money to
just anyone. Instead:
- Stay on the alert and be safe online.
- Be wary of crowd-funding web sites.
- Be on the lookout for fraudulent charitable organization web pages (check URLs carefully).
- Validate the organization that you donate to—do your research first; ask how they intend to spend the money.
- Don’t click links in emails or text messages you receive asking you to give; instead, you navigate to the charity of your choice.
- Always: check URLs, verify message senders, and think before you click.
Saturday, June 11, 2016
What to do if your identity is stolen
Yesterday a co-worker discovered that he'd been the victim of identity theft when he determined that an American Express card had been opened in his name and charges were run up to $20,000. He came to me for help.
It is a harrowing place to find yourself. The only way a credit account can be opened in your name is if someone has your name, Social Security Number (SSN) and date of birth. If that's the case, then you have be on your toes for the rest of your life. With your SSN, taxes can be filed in your name, credit can be opened in your name, insurance and medical benefits can be purchased in your name, etc.
In this case, my friend's data had been disclosed through the Premera Blue Cross breach of January 2015. It was not his fault.What do you do if this happens to you?
As for calling the bank involved, know that you may not get very far with it because the perpetrator opened the account with your name and SSN but with different contact information (address, phone, email, etc.). The bank cannot discuss the account with you if they can't validate you as the account holder. Be prepared for this and don't let it frustrate you.
It is a harrowing place to find yourself. The only way a credit account can be opened in your name is if someone has your name, Social Security Number (SSN) and date of birth. If that's the case, then you have be on your toes for the rest of your life. With your SSN, taxes can be filed in your name, credit can be opened in your name, insurance and medical benefits can be purchased in your name, etc.
In this case, my friend's data had been disclosed through the Premera Blue Cross breach of January 2015. It was not his fault.What do you do if this happens to you?
Your first four tasks:
- Contact all three credit bureaus to put fraud alerts on your credit and freeze your credit with all three bureaus. It is a good idea to freeze the credit of your spouse and children, as well.
- File a report with the Federal Trade Commission (FTC). All of the help you need to report identity theft and get a recovery plan together is at the FTC site https://www.identitytheft.gov/. Here is a great summary document to guide you through all the steps: Taking Charge: What to Do if your Identity is Stolen.
- Call your local police and make a report. Obtain a copy of the report.
- Call the bank where the scammer opened an account in your name and report it to the fraud department.
More tips:
Afterward, as an extra precaution, change your user names and passwords on all your sensitive accounts everywhere (banking, insurance, retirement, brokerage, credit bureaus, IRS.gov, TurboTax/Intuit, benefits, payroll, personal email, etc.). It is imperative that you employ unique, strong, long passwords. If two-factor authentication is available, use it.
Remember this forever: The fraudster has your SSN and may sit on that information for years before using it. This is why, in an earlier blog posting, I recommend that you freeze your credit, regardless of whether or not you think your SSN is in someone else's hands. For most of us, I suspect it's only a matter of time before we become victims too.
In addition to freezing your credit, file your taxes early every year and, I repeat: do not use weak passwords on any online accounts. Make sure your passwords are unique, and don't share them with anyone.
Tuesday, June 7, 2016
Why you never use the same password on more than one web site
It is a fundamental tenet of user security in 2016 that you do not re-use the same password simultaneously across different web sites and software programs. All the hacker has to do is crack your *one* password to hack all of your accounts. Oh, and he (or she) will.
Here is the latest reported breach caused by password re-use, a mistake made by none other than Mark Zuckerberg, founder of Facebook: Zuckerberg hacking adds to cloud of internet insecurity. Please read it.
The Zuckerberg error is just one example of many prominent people getting hacked because they use a weak password—and, worse, use it across multiple accounts. Use a long, complex password (the longer the better), and guard it like you would all of your liquid assets.
Here is another tip: For accessing your most sensitive data (online banking, insurance, brokerage accounts, medical records, etc.) use a different user name as well. Don't use the same login name that you use for your Gmail, eBay, Blogger, Twitter, Intuit, Facebook and other accounts.
It is never a good idea to use your email name as your banking login name. For example, if your email name is JohnDoe@myemail.com, make your banking login name JohnDoughBoy (or something else easy to remember, hard for others to guess). For extra security, throw in a special character (if allowed).
Another solution is discussed here: First Click: An easy way to quit reusing passwords.
Even Krebs is discusses this week how some online organizations are forcing password resets if they think you are re-using yours elsewhere: Password Re-user? Get Ready to Get Busy
Here is the latest reported breach caused by password re-use, a mistake made by none other than Mark Zuckerberg, founder of Facebook: Zuckerberg hacking adds to cloud of internet insecurity. Please read it.
The Zuckerberg error is just one example of many prominent people getting hacked because they use a weak password—and, worse, use it across multiple accounts. Use a long, complex password (the longer the better), and guard it like you would all of your liquid assets.
Here is another tip: For accessing your most sensitive data (online banking, insurance, brokerage accounts, medical records, etc.) use a different user name as well. Don't use the same login name that you use for your Gmail, eBay, Blogger, Twitter, Intuit, Facebook and other accounts.
It is never a good idea to use your email name as your banking login name. For example, if your email name is JohnDoe@myemail.com, make your banking login name JohnDoughBoy (or something else easy to remember, hard for others to guess). For extra security, throw in a special character (if allowed).
Another solution is discussed here: First Click: An easy way to quit reusing passwords.
Even Krebs is discusses this week how some online organizations are forcing password resets if they think you are re-using yours elsewhere: Password Re-user? Get Ready to Get Busy
Saturday, May 28, 2016
Beware "overlay" skimmers installed at Walmart check-outs
Look before you swipe, and don't ever swipe your debit card. Wherever possible, dip your chip-enabled credit card instead of swiping it.
We've said this all before. Today, security journalist Brian Krebs gives us reason for a reminder.
The card skimmers that thieves use to steal the data about you and your account—data that is stored in the magnetic stripe—are so well crafted these days that it is difficult to tell they're a ruse. Take a look at the photo here. Can you tell it's a fake?

Probably not. Here is what it looks like before the thief snaps it onto the existing point-of-sale device:

This device records your account information when you swipe your card, including your PIN. The data is downloaded later when the fake front is retrieved by the thief.
These were found installed in Walmart stores in Virginia and Kentucky. But they can be installed anywhere that uses this particular Ingenico credit card terminal. Grocery store shoppers suffered card thefts when similar devices were installed at Safeway stores a few months ago.
For more information and a surveillance snapshot of criminals installing an overlay skimmer at a Walmart self check-out station, see Brian Krebs' blog posting Skimmers Found at Walmart: A Closer Look.
If your card is chip-enabled, dip it. And never swipe your debit card.
We've said this all before. Today, security journalist Brian Krebs gives us reason for a reminder.
The card skimmers that thieves use to steal the data about you and your account—data that is stored in the magnetic stripe—are so well crafted these days that it is difficult to tell they're a ruse. Take a look at the photo here. Can you tell it's a fake?
Probably not. Here is what it looks like before the thief snaps it onto the existing point-of-sale device:
This device records your account information when you swipe your card, including your PIN. The data is downloaded later when the fake front is retrieved by the thief.
These were found installed in Walmart stores in Virginia and Kentucky. But they can be installed anywhere that uses this particular Ingenico credit card terminal. Grocery store shoppers suffered card thefts when similar devices were installed at Safeway stores a few months ago.
For more information and a surveillance snapshot of criminals installing an overlay skimmer at a Walmart self check-out station, see Brian Krebs' blog posting Skimmers Found at Walmart: A Closer Look.
If your card is chip-enabled, dip it. And never swipe your debit card.
Saturday, May 7, 2016
Can your phone be hacked?
Yes, of course that computer in our pocket is easily hacked. When that happens, the hacker can see all of your phone data—email messages, account information, credit card numbers, text messages, bank information—and the bad guy can even listen to your calls. What is even creepier than that is the fact that the hacker can turn on your video camera and watch you without your knowledge.
How hard is it to hack a phone? It's not. Watch this 13-minute CBS News 60 Minutes episode "Hacking Your Phone," for a live demonstration of hackers listening in on a congressman's phone.
They say there are two types of people in this world: Those who know that their phones have been hacked, and those who don't know that their phones have been hacked.
Want more protection for your phone? Stay educated and alert, don't randomly connect to public Wi-Fi networks, don't click unexpected links (or attachments) delivered to you via texts or email messages, encrypt your data, keep your operating system and apps up to date, and consider installing a security app like Lookout. That happens to be the app that I use.
Other tips:
- FCC Smartphone Security Checker
- Smartphone Security (by Kaspersky)
- 8 common sense tips to keep your smartphone secure (by Verizon)
How hard is it to hack a phone? It's not. Watch this 13-minute CBS News 60 Minutes episode "Hacking Your Phone," for a live demonstration of hackers listening in on a congressman's phone.
They say there are two types of people in this world: Those who know that their phones have been hacked, and those who don't know that their phones have been hacked.
Want more protection for your phone? Stay educated and alert, don't randomly connect to public Wi-Fi networks, don't click unexpected links (or attachments) delivered to you via texts or email messages, encrypt your data, keep your operating system and apps up to date, and consider installing a security app like Lookout. That happens to be the app that I use.
Other tips:
- FCC Smartphone Security Checker
- Smartphone Security (by Kaspersky)
- 8 common sense tips to keep your smartphone secure (by Verizon)
Monday, April 18, 2016
Now is the time to uninstall QuickTime from Windows
Apple QuickTime is a media player that can be downloaded and installed for free on your Windows computer, not unlike Windows Media Player.
Last week, Apple ended support for QuickTime on Windows due to critical security flaws. Apple will no longer support or provide security updates for this software and recommends that it be removed. I have uninstalled it from my computer, and you should too.
For more information, see US-CERT for more information at https://www.us-cert.gov/ncas/alerts/TA16-105A, or read the TrendMicro article at http://www.zdnet.com/article/apple-deprecates-quicktime-for-windows-with-two-security-holes-unpatched-trend-micro/.
Instructions for removing QuickTime for Windows can be found on the Apple Uninstall QuickTime page.
Do it today!
Last week, Apple ended support for QuickTime on Windows due to critical security flaws. Apple will no longer support or provide security updates for this software and recommends that it be removed. I have uninstalled it from my computer, and you should too.
For more information, see US-CERT for more information at https://www.us-cert.gov/ncas/alerts/TA16-105A, or read the TrendMicro article at http://www.zdnet.com/article/apple-deprecates-quicktime-for-windows-with-two-security-holes-unpatched-trend-micro/.
Instructions for removing QuickTime for Windows can be found on the Apple Uninstall QuickTime page.
Do it today!
Sunday, April 17, 2016
Phishing alert: They use your home address in this one
Beware a new email phishing campaign that is
targeting people by using your home address and claiming you are overdue payment on an invoice.
The message in this one uses good grammar and is fairly well worded but is quite dangerous. If you fall victim by clicking the link, it executes a new variant
of ransomware that doesn’t require a network connection to function. As we all know from previous posts on this blog, ransomware is designed to encrypt all of your files and hold the decryption key for ransom. Pay up, or lose all your files that have not been backed up to a separate system.
Folks, don't fall for this. The best way to avoid becoming a victim of a phishing attack is simple: Do not click links in email unless you've validated the sender, and don't open attachments to emails unless you are 100% certain they are safe.
See
Tripwire’s coverage here, which contains a snapshot of a sample phishing message: http://www.tripwire.com/state-of-security/latest-security-news/phishing-campaign-sends-out-scam-emails-containing-recipients-home-address/.
Have you backed up your files yet? Better safe than sorry!
Previous posts are:
- Beware big uptick in ransomware this week! (March 2016)
- What is ransomware? (July 2015)
Saturday, March 26, 2016
How easy it is to install a credit card skimmer
Ever wonder how easy it is to install one of those skimmers that steals your credit card information straight from the magnetic stripe on the back of the card? Check out this YouTube video to see how a pair of convenience store shoppers install a credit card skimmer on the point-of-sale (POS) device in two and a half seconds. It's pretty amazing.
And here is a 5-minute ABC News Nightline story on YouTube showing thieves installing a skimmer on a gas pump. As I was watching this, I wondered how the bad guys are able to open up the pump's front panel. Turns out, every gas pump uses a universal key, easily purchased online for a few bucks.
Want to know more about these skimmers? See Brian Krebs' blog All About Skimmers.
The FBI warns: Taking a Trip to the ATM? Beware of Skimmers. Recently, here in Georgia, an investigation was launched covering six states, as described in this news story: Secret service launches 6 state investigation into ATM skimmers.
If you think you've been a victim of credit card skimming, contact your local U.S. Secret Service field office. If you're not sure whether to report, see When and how to report fraud to the U.S. Secret Service.
Be smart when swiping your card.
And here is a 5-minute ABC News Nightline story on YouTube showing thieves installing a skimmer on a gas pump. As I was watching this, I wondered how the bad guys are able to open up the pump's front panel. Turns out, every gas pump uses a universal key, easily purchased online for a few bucks.
Want to know more about these skimmers? See Brian Krebs' blog All About Skimmers.
The FBI warns: Taking a Trip to the ATM? Beware of Skimmers. Recently, here in Georgia, an investigation was launched covering six states, as described in this news story: Secret service launches 6 state investigation into ATM skimmers.
If you think you've been a victim of credit card skimming, contact your local U.S. Secret Service field office. If you're not sure whether to report, see When and how to report fraud to the U.S. Secret Service.
Be smart when swiping your card.
- Never let a cashier or server swipe it for you or take it out of view.
- Keep an eye on your credit card account, checking every statement line-by-line
- Report any suspected fraud immediately to your bank, certainly within 60 days
- Don't swipe your card at gas pumps that are "in the shadows," or pay inside
- Look before you swipe
Wednesday, March 16, 2016
Beware big uptick in ransomware this week!
Last July, we posted What is ransomware? If your computer is infected with ransomware, the hacker encrypts all of your data and then offers to decrypt it in exchange for payment. If you do get hit with ransomware, you have two choices: (1) pay, or (2) wipe your hard drive and restore it from backup.
Did you know that your computer can get infected with ransomware when you visit safe, familiar web sites like MSN.com or AOL.com, national weather web sites, everyday news sites like the New York Times, and other "safe" places? It's true. That's because these sites host advertisements, which are run by third parties that they do business with. All those little ads that you see popping up on every news site you visit—that is called adware.
If you get a pop-up like this, you are a victim of ransomware:
It isn't that the big name web site owners like New York Times aren't being careful, it's that the adware companies suffer some sort of breach or domain name takeover before anyone else realizes it, and they start serving up malicious ad links on the "safe" sites that we are familiar with and use every day.
And if you're smart, you do not click those links. They can be downright convincing, but if your personal rule is "don't click," no matter how enticing an ad may be, then you are practicing safe browsing. Make this your mantra when surfing the web: Do. Not. Click. Ads.
For details read Big-name sites hit by rash of malicious ads spreading crypto ransomware [Updated].
Did you know that your computer can get infected with ransomware when you visit safe, familiar web sites like MSN.com or AOL.com, national weather web sites, everyday news sites like the New York Times, and other "safe" places? It's true. That's because these sites host advertisements, which are run by third parties that they do business with. All those little ads that you see popping up on every news site you visit—that is called adware.
If you get a pop-up like this, you are a victim of ransomware:
It isn't that the big name web site owners like New York Times aren't being careful, it's that the adware companies suffer some sort of breach or domain name takeover before anyone else realizes it, and they start serving up malicious ad links on the "safe" sites that we are familiar with and use every day.
And if you're smart, you do not click those links. They can be downright convincing, but if your personal rule is "don't click," no matter how enticing an ad may be, then you are practicing safe browsing. Make this your mantra when surfing the web: Do. Not. Click. Ads.
For details read Big-name sites hit by rash of malicious ads spreading crypto ransomware [Updated].
Saturday, March 5, 2016
If Microsoft "tech support" calls, hang up!
I actually saw a very bright young college grad fall for this scam a few years ago.
It goes like this: You get a phone call from someone who says is name is so-and-so (Mack, Jack, Mike, Matt, Joe or what-have-you), and that he's with Microsoft Support or Windows Tech Support—something along those lines. He may speak with a thick accent.
He'll tell you that your computer is showing up on his monitor as being infected with a virus and that in order to prevent something really awful from happening to your data, he's going to help you fix it. Typically, he'll direct you to a web site and may even offer to help you change settings in your browser configuration (e.g., a proxy server IP address) if the site appears to be blocked.
If the conversation gets this far, it is way past time to hang up. Never, ever make changes to your security settings or navigate to a web site URL given to you by an unknown caller. Oh, and they may continue to try to call you at least once more before giving up.
Microsoft does not make unsolicited calls to help you fix your computer.
In fact, if anyone calls you claiming to represent some established corporation, retailer, charity, or government agency and then asks you to either (1) navigate to a web site, or (2) provide a credit card number or other personally identifying information, just hang up. Never give your information to an unsolicited caller, even if he says you already have an account with his organization. That's called social engineering; don't fall for it.
For more information about the tech support scam, see this page at the Microsoft Safety & Security Center: Avoid scams that use the Microsoft name fraudulently.
It goes like this: You get a phone call from someone who says is name is so-and-so (Mack, Jack, Mike, Matt, Joe or what-have-you), and that he's with Microsoft Support or Windows Tech Support—something along those lines. He may speak with a thick accent.
He'll tell you that your computer is showing up on his monitor as being infected with a virus and that in order to prevent something really awful from happening to your data, he's going to help you fix it. Typically, he'll direct you to a web site and may even offer to help you change settings in your browser configuration (e.g., a proxy server IP address) if the site appears to be blocked.
If the conversation gets this far, it is way past time to hang up. Never, ever make changes to your security settings or navigate to a web site URL given to you by an unknown caller. Oh, and they may continue to try to call you at least once more before giving up.
Microsoft does not make unsolicited calls to help you fix your computer.
In fact, if anyone calls you claiming to represent some established corporation, retailer, charity, or government agency and then asks you to either (1) navigate to a web site, or (2) provide a credit card number or other personally identifying information, just hang up. Never give your information to an unsolicited caller, even if he says you already have an account with his organization. That's called social engineering; don't fall for it.
For more information about the tech support scam, see this page at the Microsoft Safety & Security Center: Avoid scams that use the Microsoft name fraudulently.
Saturday, February 20, 2016
If Dell calls you, just hang up
By now, we all know that if the IRS contacts you by phone, you should hang up. If an attorney calls you saying your grandson is in a bit of trouble and needs your financial assistance, hang up. If Microsoft calls you saying your computer is infected, hang up.
Starting to see the pattern here?
As reported earlier this week by Brian Krebs in his Krebs on Security blog, the latest computer "tech support" phone scam is aimed at Dell users. The fake caller appears to know your computer's unique Dell service tag number and may make a claim that your computer is in need of service. If you get this call, hang up and report it to Dell at (866) 383-4713.
It's time that we get ahead of the curve and start reporting these fraudsters. We may think that these things are so well documented that you'd have to be living in a cave to not know about them. But remember that some folks are less connected and more vulnerable than others, especially the elderly and those who are not computer savvy, as most of us aren't.
Plus, these social engineers can be very convincing.
So, when you hear of a new scam like this, spread the word to all your friends and relatives to stay on the alert. The more we team up, the less chance of folks falling victim to these never-ending scams.
If you own a Dell computer, see the Krebs posting Dell to Customers: Report 'Service Tag' Scams.
Starting to see the pattern here?
As reported earlier this week by Brian Krebs in his Krebs on Security blog, the latest computer "tech support" phone scam is aimed at Dell users. The fake caller appears to know your computer's unique Dell service tag number and may make a claim that your computer is in need of service. If you get this call, hang up and report it to Dell at (866) 383-4713.
It's time that we get ahead of the curve and start reporting these fraudsters. We may think that these things are so well documented that you'd have to be living in a cave to not know about them. But remember that some folks are less connected and more vulnerable than others, especially the elderly and those who are not computer savvy, as most of us aren't.
Plus, these social engineers can be very convincing.
So, when you hear of a new scam like this, spread the word to all your friends and relatives to stay on the alert. The more we team up, the less chance of folks falling victim to these never-ending scams.
If you own a Dell computer, see the Krebs posting Dell to Customers: Report 'Service Tag' Scams.
Saturday, January 30, 2016
If you get a big check from Comcast, call the police
The scams just get better and better. Here is the story of a Georgia man who received a very convincing $3788.50 check from Comcast. The enclosed letter instructed him to buy $3000 in pre-paid gift cards, deposit the check, and keep the balance of the check for payment of services.
According to WSB-TV, this scam has been around for a long time, but its use of the Comcast name is new.
Two big red flags in the letter are to "act quickly" and tell no one about the job. But hey, it's also common knowledge that Comcast isn't in the retail service quality business. In addition, why would anyone pay for a job before it is performed, much less send a check by mail to someone before being hired?
Fortunately, this potential victim was smart enough to report it to the police, primarily because he was suspicious, but also because he is not a Comcast customer. Sadly, some folks do fall victim to a ruse like this. The check does look real.
For more information, see the WSB-TV story at http://www.wsbtv.com/news/news/local/scam-uses-cable-companys-name-trick-customers/np8gT/.
According to WSB-TV, this scam has been around for a long time, but its use of the Comcast name is new.
Two big red flags in the letter are to "act quickly" and tell no one about the job. But hey, it's also common knowledge that Comcast isn't in the retail service quality business. In addition, why would anyone pay for a job before it is performed, much less send a check by mail to someone before being hired?
Fortunately, this potential victim was smart enough to report it to the police, primarily because he was suspicious, but also because he is not a Comcast customer. Sadly, some folks do fall victim to a ruse like this. The check does look real.
For more information, see the WSB-TV story at http://www.wsbtv.com/news/news/local/scam-uses-cable-companys-name-trick-customers/np8gT/.
Saturday, January 23, 2016
Future Crimes author Marc Goodman speaks at Town Hall Seattle
Did you know that last year the world experienced its first billion-dollar bank heist? And that the bad guys didn't even have to walk into a bank?
We've all heard the term flash mob—a scary concept in itself. But what about a flash rob? How do we defend against that? (There are plenty of YouTube videos showing teen mobs casually ransacking stores.)
Perhaps you've heard of SaaS (software as a service). Well, now anyone can buy crimeware online to commit theft, fraud and other offenses—so now we have crime as a service (Caas). In his talk, Marc explores the implication of crime being automated across an ever-growing attack vector as our cars, refrigerators, watches, pacemakers, TVs and other daily use tools connect to the Internet and to each other.
By 2019, cyber crime is going to cost $2 trillion. By 2045 we will have a computer with the processing power of the human brain. Think of the criminal implications of that prospect.
A good friend of mine from my days at startup Aventail in Seattle emailed me yesterday to tell me she had an opportunity to see Marc Goodman, author of Future Crimes, speak at a Town Hall in Seattle this month. The talk was recorded (audio only, not video).
In the recording, Marc describes the future of crime as:
We've all heard the term flash mob—a scary concept in itself. But what about a flash rob? How do we defend against that? (There are plenty of YouTube videos showing teen mobs casually ransacking stores.)
Perhaps you've heard of SaaS (software as a service). Well, now anyone can buy crimeware online to commit theft, fraud and other offenses—so now we have crime as a service (Caas). In his talk, Marc explores the implication of crime being automated across an ever-growing attack vector as our cars, refrigerators, watches, pacemakers, TVs and other daily use tools connect to the Internet and to each other.
By 2019, cyber crime is going to cost $2 trillion. By 2045 we will have a computer with the processing power of the human brain. Think of the criminal implications of that prospect.
A good friend of mine from my days at startup Aventail in Seattle emailed me yesterday to tell me she had an opportunity to see Marc Goodman, author of Future Crimes, speak at a Town Hall in Seattle this month. The talk was recorded (audio only, not video).
In the recording, Marc describes the future of crime as:
- Exponential - technologies are advancing exponentially, allowing criminals to scale their business
- Automated - algorithms are increasingly running our world and making decisions for us, but algorithms can lie
- Three-dimensional - cyber crime is no longer occurring in 2-D, and the bad guys are outrunning the good guys—like when a $100 drone breaks the century-old security paradigm that keeps convicts inside prison walls
With the advent of the Internet of Things (IoT), the ways in which others can attack us are increasing exponentially. If you think it's not possible for a bad guy to break into your computer network through your facility's heating/cooling system, think again. That's how Target was hacked.
If you haven't taken the time to read Marc's compelling book, (which I highly recommend!), you might want to take an hour to listen to the Seattle Town Hall audio recording. The play button is near the top of the page, just below Media Library. Scroll down for a link to his TED Talk.
Enjoy!
Enjoy!
Wednesday, January 20, 2016
More info about freezing your kids' credit
In a May 2015 blog posting we asked ourselves, "Should I freeze my kids' credit?" Conclusion: Yes, you should do this to prevent identity theft. In a 2012 study, some 10% of children's identities were stolen.
Today, leading security expert and journalist Brian Krebs posted information about which states have laws about credit freezing for minors at The Lowdown on Freezing Your Kid's Credit. Parents, you will want to spend five minutes reading the Krebs posting to determine what is allowed in your kids' state of residence.
Anyone with a social security number should consider freezing his or her credit with all three credit reporting bureaus. It is the single most effective defense against identity theft, and it is not a hassle to do a temporary lift of the freeze should you need it.
I've tested it, and the $9.00 or so that I spend to lift the freeze is the cheapest anti-identity theft insurance I can buy. It helps me sleep better at night too.
Who will protect your kids identities?
Today, leading security expert and journalist Brian Krebs posted information about which states have laws about credit freezing for minors at The Lowdown on Freezing Your Kid's Credit. Parents, you will want to spend five minutes reading the Krebs posting to determine what is allowed in your kids' state of residence.
Anyone with a social security number should consider freezing his or her credit with all three credit reporting bureaus. It is the single most effective defense against identity theft, and it is not a hassle to do a temporary lift of the freeze should you need it.
I've tested it, and the $9.00 or so that I spend to lift the freeze is the cheapest anti-identity theft insurance I can buy. It helps me sleep better at night too.
Who will protect your kids identities?
Monday, January 18, 2016
What you should be shredding
Happy New Year, everyone! An October post asks, Are you shredding your used boarding passes? If not, you should be because the bar code on that piece of paper contains lots of personal information about you and your trip.
For your own security, here is a list of other documents that you should be shredding, courtesy of the February 2016 edition of Readers Digest:
To simplify, remember to shred anything that displays your name, address or any other personally identifying information. Let's stay safe and secure in 2016!
For your own security, here is a list of other documents that you should be shredding, courtesy of the February 2016 edition of Readers Digest:
- Prescription labels. I always obliterate these from prescription bottles before I recycling the containers. There is enough information on the label to allow a dumpster diver to refill the medication or use social engineering to steal your identity.
- Purchase receipts. For the receipts that you don't save, these often carry the last four digits of your social security number (SSN), which is a frequently required authentication credential. They can also be used to fraudulently return store items. NOTE: In a similar vein, Brian Krebs posted an interesting blurb in December about The role of phony returns in gift card fraud.
- Pet medical papers. I hate to even mention this one, because you should never use your pet's name as part of any online password, but these should be shredded as well.
- Return shipping labels. These usually contain your full name and address. I not only shred these, but any piece of paper or envelope that comes in the mail pre-printed with my name and address goes into the shredder.
- Account statements. I added this one to the list myself. It goes without saying that any document with any account number on it should be shredded after use, including utility bills, phone bills, bank statements, insurance information, tax documents, pay stubs, etc.
To simplify, remember to shred anything that displays your name, address or any other personally identifying information. Let's stay safe and secure in 2016!
Subscribe to:
Posts (Atom)